No, not MOOCs. Badges.
 Ok, now that you’ve stopped laughing (I admit, even I have a hard time not dismissively thinking of the sleeves of my Cub Scout shirt when I hear the term) let me explain why badges, as they mature beyond where they are currently, have the potential to disrupt formal education in a way that none of the technology innovations we’ve seen in the last couple of decades have.
Ok, now that you’ve stopped laughing (I admit, even I have a hard time not dismissively thinking of the sleeves of my Cub Scout shirt when I hear the term) let me explain why badges, as they mature beyond where they are currently, have the potential to disrupt formal education in a way that none of the technology innovations we’ve seen in the last couple of decades have.
Over those two decades, essentially the duration of my working life so far, every time I have tried to explain the magnitude of the disruptions (and the amount of potentials) that the network presents to formal education institutions (especially post secondary ones) the trump card interlocuters ALWAYS bring out to minimize the potential threat is “Accreditation.” Regardless of how many people are learning with each other, for free, in communities online, or the skyrocketing costs of formal ed, or how poorly the 4 year residential model serves an increasingly unconventional student body, or how the educational practices in many higher ed classrooms have barely moved out of the 19th Century, when met with the prospect that the value of a University degree is under threat and that their “market” will get as disrupted as the newspaper business, or travel agencies, etc., the response is simply “yeah, but we’re the only one who can issue degrees that people trust.” But I believe badges hold the potential to disrupt this.
Again, I’ll give you a second to stop laughing. And I can’t fault you for laughing; even if you can get over the name, the idea that “badges” can compete head to head with “degrees” seems laughable, if badges are seen simply as their equivalent, just smaller, issued to acknowledge informal learning by small groups who could never compete with the brand recognition of the likes of Harvard or, closer to home, UBC, and, importantly, lacking the backing of governments and other trusted “bodies.” Maybe even more laughable for lacking recognition by the people degree/badge holders are trying to convince (mostly employers, but others too).
But I contend that’s because, so far, badges haven’t tackled THE important problem, at scale, in a way that models how the net works – who do we trust and why?
What is Accreditation Anyways?
Before looking at how a different execution of badges could seriously disrupt higher ed, it seems important to get clear on what accreditation is in the first place. The explanation below, from Wikipedia, offers a decent starting point:
“Higher education accreditation is a type of quality assurance process under which services and operations of post-secondary educational institutions or programs are evaluated by an external body to determine if applicable standards are met. If standards are met, accredited status is granted by the agency.
In most countries in the world, the function of educational accreditation for higher education is conducted by a government organization, such as a ministry of education.” from http://en.wikipedia.org/wiki/Higher_education_accreditation
 While it may work slightly different in the US and other jurisdictions, the general model seems to hold true – some body, whether governmental, NGO (and for profit? god I hope not) establishes criteria and processes which a department or program must fulfill, and then vouchsafes their credentials as credible based on this. It’s about how we currently establish trust in the credibility, quality (and ultimately value) of the education that someone (be it the public or, sadly, increasingly the individual student) has paid for. Ideally, this would be individualized – when trying to evaluate a specific individual’s capacities, we wouldn’t look at a proxy for that (which is what a credential is) but instead be able to examine all the examples, to look at the ways in which their capacity was developed and judge for ourselves whether it meets the specific needs we have. But that doesn’t scale, at all, so we invented proxies, first at an institutional level, and as these grew in number, at a jurisdictional and even international level.
While it may work slightly different in the US and other jurisdictions, the general model seems to hold true – some body, whether governmental, NGO (and for profit? god I hope not) establishes criteria and processes which a department or program must fulfill, and then vouchsafes their credentials as credible based on this. It’s about how we currently establish trust in the credibility, quality (and ultimately value) of the education that someone (be it the public or, sadly, increasingly the individual student) has paid for. Ideally, this would be individualized – when trying to evaluate a specific individual’s capacities, we wouldn’t look at a proxy for that (which is what a credential is) but instead be able to examine all the examples, to look at the ways in which their capacity was developed and judge for ourselves whether it meets the specific needs we have. But that doesn’t scale, at all, so we invented proxies, first at an institutional level, and as these grew in number, at a jurisdictional and even international level.
But it seems to work. Well, kind of. Mostly. In jurisdictions where accreditation is spread out across a large number of bodies, it can be hard to keep track of them all (cf. http://en.wikipedia.org/wiki/List_of_recognized_higher_education_accreditation_organizations#United_States). This, as well as the sheer number, globally, of accrediting bodies, can let imposters creep in and makes verification difficult. And even with rigour and government backing, there remains the real issue of inter-jurisdictional recognition; just ask our cab-driving Doctor from Pakistan about this. Add to this the fact that, while the accreditation process is by design rigorous and difficult to pass, that also means, by design, it doesn’t expand quickly or accomodate smaller units of learning well; just ask someone who’s tried to start a new program, which seems more relevant if we acknowledge the pace of the growth of knowledge is unlikely to slow down.
How could badges disrupt this?
So my take on why badges have seemed underwhelming to date is that they’ve appeared to focus on the signalling mechanism (a way for person A to signal they’ve learned X from organization B, which is in essence what a diploma or degree generally does) without addressing the underlying trust/credibility issue (WHO has issued that certificate and why should they be trusted – e.g. why is a badge from UVic worth more than one from Bob’s Online Badge Emporium.) It had to unfold this way – the obvious place to start is with the basic mechanisms for issuing and displaying a badge. But that does not need to be the sum total of what badges are, and according to Mozilla Roadmap documents on their Open Badge Infrastructure, won’t be.
At root, what we’re dealing with is a question of “who should we trust and why?” As luck would have it, we already have a number of models of how to address this in the digital world that come from the field of Cryptography. Specifically, when it comes to public key encryption, there are two competing models that I believe align well with the current model of accreditation and the emerging model of badges: the centralized trust model of a pubic key infrastructure and the decentralized “web of trust” model.
 The centralized trust model (think “Certificate Authorities” [CAs] like Verisign or Thwate) is akin to the current accreditation model, where only a single (or very few) body is entrusted to issue accreditation/certificates and acts as the maintainer and adjudicator of standards. Like the current accreditation model the centralized trust model is at first blush attractive because it consolidates this complex function in a few entities, but it also suffers a number of problems: if a CA is compromised, the security for everyone in the system for which the CA is attesting is similarly lost. Also, like centralized accreditation, it converges knowledge (or ‘validation’) and power into very concentrated hands; we depend on the (increasingly questionable) representative nature of our democracy to ensure that what accreditors accredit is “in the public good” just like we rely on these few Certificate Authorities to verify and enforce throughout their entire chain (it’s not quite as simple as that in both cases, but hopefully a good enough approximation.)
The centralized trust model (think “Certificate Authorities” [CAs] like Verisign or Thwate) is akin to the current accreditation model, where only a single (or very few) body is entrusted to issue accreditation/certificates and acts as the maintainer and adjudicator of standards. Like the current accreditation model the centralized trust model is at first blush attractive because it consolidates this complex function in a few entities, but it also suffers a number of problems: if a CA is compromised, the security for everyone in the system for which the CA is attesting is similarly lost. Also, like centralized accreditation, it converges knowledge (or ‘validation’) and power into very concentrated hands; we depend on the (increasingly questionable) representative nature of our democracy to ensure that what accreditors accredit is “in the public good” just like we rely on these few Certificate Authorities to verify and enforce throughout their entire chain (it’s not quite as simple as that in both cases, but hopefully a good enough approximation.)
Contrast this with the “web of trust” model, often exemplified by encryption systems like PGP, which is what badges *could* become. In this model, a “decentralized fault-tolerant web of confidence for all public keys” emerges, over time, as each persons’ keys are “digitally signed by other users who, by that act, endorse the association of that public key with the person or entity listed in the certificate.” (http://en.wikipedia.org/wiki/Web_of_trust) In layman’s terms, like any network effect, if there are only two of you with keys signing each others’ key, while it is still of _some_ value, the value of the system overall increases as more nodes join and a large, robust network emerges over time.
Interlude (in which the author confesses he hadn’t done his homework and, frankly, can at times be a bit of a presumptuous dick)
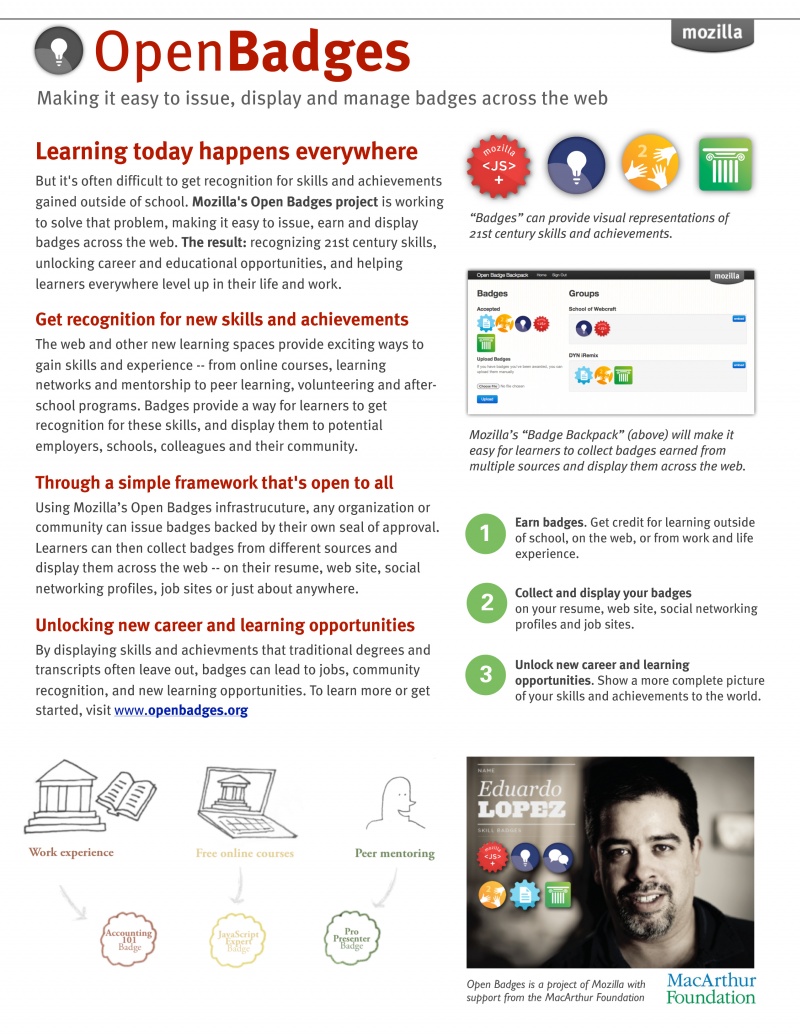 I have a confession to make: up until recently, I hadn’t paid a lot of attention to badges either. I understood they potentially offered some alternative to existing credentialing models and tried to come to their defense when various colleagues of mine dismissed them out of hand, but I couldn’t see how they could overcome the hurdle of validation/recognition. It wasn’t until I was lying on my couch a few weeks back, alternatively reading wikipedia and napping, that this idea that if badges existed within an ecosystem of issuers, learners and “recognizers” (people to whom you are trying to prove you know something) all of whom could attest to the effectiveness of the learning represented by the badge by “signing” it, that this can scale, in a Peer to Peer way that models how the actual infrastructure of the internet works. Because I hadn’t actually been involved or paying close attention to the actual developments by the Mozilla Badge team (and others, presumably) I had the (absurd? presumptuous? egotistical?) thought “why has no one else talked about this?”
I have a confession to make: up until recently, I hadn’t paid a lot of attention to badges either. I understood they potentially offered some alternative to existing credentialing models and tried to come to their defense when various colleagues of mine dismissed them out of hand, but I couldn’t see how they could overcome the hurdle of validation/recognition. It wasn’t until I was lying on my couch a few weeks back, alternatively reading wikipedia and napping, that this idea that if badges existed within an ecosystem of issuers, learners and “recognizers” (people to whom you are trying to prove you know something) all of whom could attest to the effectiveness of the learning represented by the badge by “signing” it, that this can scale, in a Peer to Peer way that models how the actual infrastructure of the internet works. Because I hadn’t actually been involved or paying close attention to the actual developments by the Mozilla Badge team (and others, presumably) I had the (absurd? presumptuous? egotistical?) thought “why has no one else talked about this?”
Which of course they have. The folks working on this are very smart. And (luckily for me) I thought to ask on twitter before finishing this piece (and thus coming off even more arrogant than usual) whether anyone was working on a “distributed trust model for badges.” @prawsthorne was the first to offer some helpful links, pointing me to the Mozilla Roadmap documents on their Open Badge Infrastructure, the Badges Infrastructure Tech Docs (cf section on ‘Badge Endorsement’), the Mozilla Open Badges Dev Group and a post on the Super Awesome Badge Summer (cf section “Endorsement, public key infrastructure, federated backpacks”).
All of which were good starting points and indicators that the issue was definitely on the Mozilla Badges team’s radar. But it wasn’t until I started digging in further and also received a few more messages, both from Peter and from leaders of the badge initiative, Carla Cassili and Erin Knight, that I struck gold and read how clearly the vision they have for a distributed validation/trust network aligned with my own couch-bound daydreaming. Instead of trying to replicate any further the arguments, I just urge anyone who is interested in understanding the potential to go read the following two pieces:
So why won’t this turn out exactly how PGP vs Central Authorities Have?
If you know the history of public key encryption, you’ll know that while both the centralized Public Key Infrastructure model of Certificate Authorities and the distributed web-of-trust model of PGP still exist, PGP adoption by individual users has been spotty at best, plagued by very real “ease of use” issues (along with a general lack of understanding of the issue), while PKI, for all its flaws, supports pretty much all of the commercial transaction encryption on the net today (read: online shopping etc over https). Given that, why should a validation and endorsement mechanism for badges be any different?
As Erin outlines in the paper linked to above (page 4), there are plenty of good reasons for us to resist implementing a centralized trust model that replicates existing centralized accreditation models, easier though that may be. But even if we chose not to, what will keep a distributed model from failing/help it succeed? Well, a few things, I think:
- we need to learn the lessons from PGP and focus on implementations of the model that make it as easy as possible for endorsers to validate badges or badge issuers. This seems obvious, but one of the pieces I think we often miss out is implementing things in a way that our motivations for the user to do what we hope they’ll do are in line with THEIR motivations/what is actually valueable to them. If endorsing a badge requires too many additional steps on top of using/recognizing a badge, it is less likely to occur at scale.
- not wavering from a vision of true peer to peer system that allows endorsement at the lowest individual level, and yet allowing endorsements to aggregate so that existing proxy groups (like universities and their accreditors) can transition from a monolithic proxy model to this more distributed process but still keep some of the advantages of the existing trust networks they already have, while still opening up the field to individual upstarts (cf http://www.gswot.org/ as an example of how this works in the PGP world.)
Even with all of this and a flawless execution, there is nothing to guarantee widespread adoption or that this will become the disruptive force it has the potential to become. Incumbents do not give up their advantages willingly and it is naive to think they will. But…
…implemented in a robust, open way that really does allow a badge to represent learning at various scales (micro-lessons to full programs) and to be attested to, *bi-directionally*, by all the parties involved (learners, issuers, endorsers, “recognizers”) at scales ranging from the individual to the national, an open badge infrastructure opens the field to upstarts who really could disrupt the existing system. Especially upstarts that already “own” users. Think Google. Think Facebook. Think Apple. Right now the accounts you have with them don’t actually have that much to do with your “real” life. But they want them to (why do you think they are so anxious for you to connect your phone number and credit cards with these accounts?) I’m nt hoping for such a future (nor do I think Mozilla is – cf their work on Persona, an “identity system for the web”), but instead of resting on the sanctity of our existing accreditation models, we need to get our heads in the game and realize the size and scale of the stakes we are playing for.
How could existing institutions respond to this?
 Well, it seems like the current response is “not at all.” And fair enough; everyone is so taxed to cope with the current set of challenges and disruptions that to even contemplate a response to a *hypothetical* disruption that may not even happen seems unfeasible at best. But if you take a step back for a second and look at this in the light of other things we say we’re trying to accomplish in our institutions, be they transforming how and what we teach to transforming our business models, this potential disruption, which I believe speaks to the core of what universities do AS A BUSINESS, may actually offer the opportunity to rethink and re-engineer this in a way that is not only beneficial to learners, instructors and institutions but can help institutions adapt to the internet instead of trying to ignore it or have it conform to models that, while long lasting, were only ever temporary approximations.
Well, it seems like the current response is “not at all.” And fair enough; everyone is so taxed to cope with the current set of challenges and disruptions that to even contemplate a response to a *hypothetical* disruption that may not even happen seems unfeasible at best. But if you take a step back for a second and look at this in the light of other things we say we’re trying to accomplish in our institutions, be they transforming how and what we teach to transforming our business models, this potential disruption, which I believe speaks to the core of what universities do AS A BUSINESS, may actually offer the opportunity to rethink and re-engineer this in a way that is not only beneficial to learners, instructors and institutions but can help institutions adapt to the internet instead of trying to ignore it or have it conform to models that, while long lasting, were only ever temporary approximations.
And where do you start? Well, you already have a unit that is quite possibly ripe to experiment with this. It’s usually called “Continuing Studies.”
This is why I dispair when I hear CIOs refer to authentication and authorization systems as “just plumbing.” Yeah, I get that it’s just plumbing – IF YOU THINK YOU LIVE IN A WORLD SEPARATE FROM THE INTERNET AS A WHOLE. I’m not suggesting they can singlehandedly solve this issue and this transformation on their own, but as some of the largest “civil society” players that exist, they have the potential to lead on an issue that WILL get decided. Given that the current contenders in the arena of trust & identity are either large commercial entities or central governments who only seem to understand models that place them at the centre validating everyone, if you understand that every time we proxy these relations, every time we “represent” them, we recreate the conditions of our own disempowerment, even if it seems less feasible, do you really want to work for the alternative? </technoutopianrant>
Alright, you can go back to laughing now.



 While it may work slightly different in the US and other jurisdictions, the general model seems to hold true – some body, whether governmental, NGO (and for profit? god I hope not) establishes criteria and processes which a department or program must fulfill, and then vouchsafes their credentials as credible based on this. It’s about how we currently establish trust in the credibility, quality (and ultimately value) of the education that someone (be it the public or, sadly, increasingly the individual student) has paid for. Ideally, this would be individualized – when trying to evaluate a specific individual’s capacities, we wouldn’t look at a proxy for that (which is what a credential is) but instead be able to examine all the examples, to look at the ways in which their capacity was developed and judge for ourselves whether it meets the specific needs we have. But that doesn’t scale, at all, so we invented proxies, first at an institutional level, and as these grew in number, at a jurisdictional and even international level.
While it may work slightly different in the US and other jurisdictions, the general model seems to hold true – some body, whether governmental, NGO (and for profit? god I hope not) establishes criteria and processes which a department or program must fulfill, and then vouchsafes their credentials as credible based on this. It’s about how we currently establish trust in the credibility, quality (and ultimately value) of the education that someone (be it the public or, sadly, increasingly the individual student) has paid for. Ideally, this would be individualized – when trying to evaluate a specific individual’s capacities, we wouldn’t look at a proxy for that (which is what a credential is) but instead be able to examine all the examples, to look at the ways in which their capacity was developed and judge for ourselves whether it meets the specific needs we have. But that doesn’t scale, at all, so we invented proxies, first at an institutional level, and as these grew in number, at a jurisdictional and even international level.


 I guess I shouldn’t be disappointed; I’m not sure why I was expecting anything different, but it was a conference. There were a few speakers that stood out for me, but quite a number that didn’t. I had hoped to find a field more closely connected to its local environment and communities; instead I found one that seems to suffer many of the same problems as “open education” – being way too supply-side driven, with many of the people sharing the data not even sure they want to. This is captured in the tagline of the summit – “Liberate the Data.” Like so many efforts before it, that inadvertently turns what should have been means (open data) into an end in and of itself. Add to this the familiar question of “engagement,” as if this was a problem to solve after you’ve built whatever it is “they” are to come to.
I guess I shouldn’t be disappointed; I’m not sure why I was expecting anything different, but it was a conference. There were a few speakers that stood out for me, but quite a number that didn’t. I had hoped to find a field more closely connected to its local environment and communities; instead I found one that seems to suffer many of the same problems as “open education” – being way too supply-side driven, with many of the people sharing the data not even sure they want to. This is captured in the tagline of the summit – “Liberate the Data.” Like so many efforts before it, that inadvertently turns what should have been means (open data) into an end in and of itself. Add to this the familiar question of “engagement,” as if this was a problem to solve after you’ve built whatever it is “they” are to come to.





